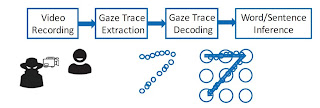
The movements of the eyes can induce those of the fingers that enter the PIN code or the unlocking pattern. A discrete attack and relatively effective.
The next time you enter your PIN or unlock pattern on your smartphone, make sure there is no camera pointing at you. Or wear tinted glasses. Because it is possible to become your secret code from the movements that make your eyes while you tap on your screen. This is what researchers from the universities of Delaware and Arizona have just proved, at the IEEE S & P 2018 conference in San Francisco. They named their attack "EyeTell".
Thus, these researchers filmed the eyes of 22 people with a Panasonic HCV7000 camcorder a few meters away, while they entered PIN codes on an iPhone 6s or unlocking schemes on a Nexus 6. The videos were then analyzed by a batteries of image detection and sorting algorithms to deduce the movement of the fingers.
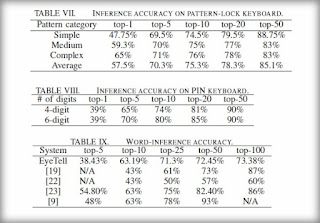
The results are rather interesting. PIN codes and patterns could be found with a respective probability of 57% and 39%. Better: the system can offer a dozen potential secret codes with a probability of 75.3% and 80% respectively to find that of the person targeted.
What have a good chance to unlock the device softly while avoiding a possible deletion of data (if the user has enabled this type of option).
The EyeTell attack also allows to find an alphanumeric password with a probability of 48%. This considerably reduces the time required for a possible brute force attack.
Paradoxically, the detection rate increases with the complexity of the secret code. A diagram with eight segments is easier to find than a diagram with four segments, the detection rate can sometimes increase by 18 points.
Similarly, a PIN code with 6 digits will be revealed faster than a PIN code with 4 digits, with a probability difference of up to 6%. This is because the complexity of the code reduces the number of possibilities in the sorting algorithm.
To protect against this type of attack, it's quite simple, just wear sunglasses. But it's not always very practical. Another solution is to practice entering your secret code without moving your eyes. Or very quickly, to bring down the detection rate.
This is not the first time researchers have been trying to guess keyboard strikes from movement or physical emanations. In 2015, researchers showed that we could transform the microphones of a smartphone or the sensors of a connected watch into a keylogger. Other, even more strange, routes have been explored in recent years, such as the interference of finger movements with Wi-Fi waves (WindTalker, WiKey). On smartphones, these attacks will be less and less effective as biometric authentication ... which is not flawless either.
Source : 01net