Who generate PKMID hashes ?
The team that publishes Hashcat - a password recovery tool - has discovered a new technique that could allow an attacker to obtain the password of some 802.11 networks with greater ease compared to existing methods.
She discovered the scheme by accident while exploring ways to put the WPA3 protocol to bad. The new method, which according to Hashcat developers, would be less effective against WPA3 works on WPA and WPA2 networks with roaming functionality. "For the moment, we do not know for which providers or for how many routers this technique will work, but we think that it allows to attack all 802.11i / p / q / r networks with functions of roaming, "they add. In a recently published blog post, an intrusion tester lists the AWUS036H Wifi card and the Linksys E4200 router among the affected devices. Roughly speaking, all routers and access points on the market from 2011 would be affected.
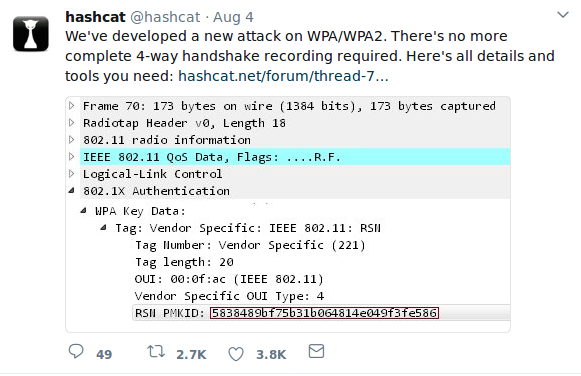
The new technique is based on extracting the Pairwise Master Key Identifier (PKMID) from an EAPoL frame. This key is needed to establish the connection between a user and an access point. It can be retrieved using a packet capture tool and then brute force decoded to retrieve the PSK key. "We receive all the necessary data within the first EAPoL frame from the access point," specify the heads behind hashcat. In other words, it is sufficient for the attacker to initiate the authentication procedure on the router or the access point to come into possession of this hash. According to the developers of the open source recovery tool, all operations require about ten minutes depending on the noise on the WiFi channel.
Compared to the existing, the method has the merit of relying only on the details provided by the router. Moreover, the tools currently available impose in addition to watching for a possible communication between the access point and a client station, which, from the point of view of the attacker, is less practical.
The success of this attack method depends on the complexity of the PSK key. In line with this observation, the main recommendation to users is to configure a strong password. Tools to achieve this goal abound online (Keepass, Keeper, LastPass, etc.) and the decryption time PKMID can be significantly extended.
Source : hashcat